Intel® Xeon® Platinum 8160T Processor
99 to protect three computers and includes more muscle when it comes to preventing ransomware, spyware and Trojans. Net only to describe products and services offered by each respective trademark holder. I am going to Walmart today for 2nd conference with them, store manager this time unit purchased at Walmart. Right click the Speaker icon located in the System Tray. “If you can’t make it good, at least make it look good. For Android devices, use GooglePlay; for Amazon tablets, utilize the Amazon App Store. There was, however, one issue this simulator created. Follow the return instructions to mail back your trade in devices after your new phones arrive. Once a collection exists on your phone, not only can you access it from your desktop browser, but you can also access it offline. This software can be useful to protect against data being obtained if your phone is taken by criminals.

Mobile devices
Advanced app security with full device cleanup. By keeping a monochromatic style and minimizing design elements, Abercrombie has allowed their clothing to stand out as lunacycle the main attraction. However, Apple is the only retailer that will accept them. Bertel is a digital minimalist who works from a hand me down laptop running elementary OS and carries around a Light Phone II. In fact, that 54% of consumers want to see more video content this year Social Media Week. To see how they performed on older models, I also tested on a Motorola Moto e5 running Android 7. The PocketJet 773 printed more slowly than the mobile inkjet printers we tested. This is important for rendering mobile maps efficiently. 509 Certificate Policy, so users can digitally sign and encrypt email notifications or other email messages required by IRS policy. And with hacking the phone camera, you will be able to use it to take pictures of the surroundings and find out who your child or spouse is with. There are many free VPNs that allow us to simulate that our connection is from another country , and they would be an option to hire the HBO Max mobile only plan, which is cheaper than the standard price in Spain and other places. Because for regular users ie desktop/laptop an open source operating system is overwhelmingly a secondary operating system. Petersburg, Florida; Tampa, Florida; and Tucson, Arizona.
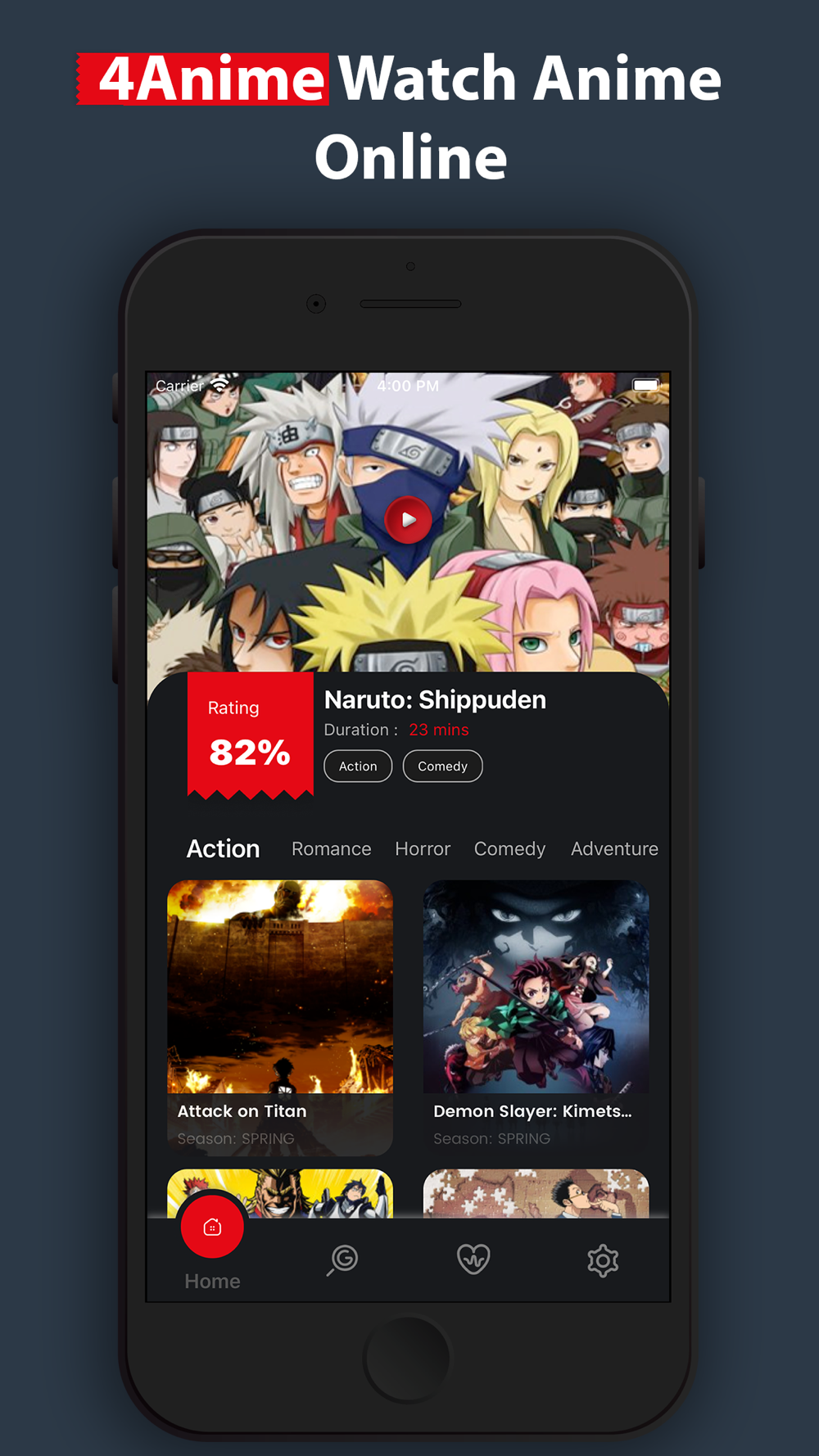
Canada’s public health agency admits it tracked 33 million mobile devices during lockdown
Moreover, you don’t have to be stuck in a contract. Following the announcement that the Tesla and SpaceX CEO’s offer to buy the social media platform was accepted, several well known users announced that they were considering leaving Twitter or using it in a different way. Adobe released a statement announcing their intention to “aggressively contribute to HTML5. This message is to advise users of the Omerta Security SIM service whom are experiencing issues with the R1 profile. Therefore, it cannot replicate all real user conditions, which means that any tests executing by this method will be inconclusive. At Shiraz University, the technical engineering professors were the only group with a firsthand lived experience of using mobile phones in education. Sarah Elson Product and Growth Lead. We appreciate all of your feedback to make DIGITS better. The parents of some children who were not among the ten trained children in the main study trained their child with limited spoken language to make requests with Yuudee at home under the direction of trainers involved in the present study. Video speed is capped at Standard Definition, regardless of the network the device is on for example 4G LTE. Games that require Flash are not playable on mobile devices. At design time – right click SmartBearBrowser in TestedApps and select Run Application. In fact, it might be a good idea to look into current Amazon Best Sellers for your target market. Didn’t follow the guidance at 6 above. There are different types of output devices, which are used for displaying processed data into various formats; below explain each one –. In times of remote work, it’s quite challenging as you usually need a number of devices at your disposal. Actively scan device characteristics for identification. Mobile App Prompt Creative. Choose ‘more’, and the Jetpack tells you your network password. UK: Department of Conputer Science; 2007. Some online reviewers report a delay in firing up the Solis hotspot, though they’re able to stay connected where signals are available. If your company has a BYOD policy, encourage employees to regularly update the software on their personal devices, explaining to them that these actions are a core part of your company’s risk mitigation strategy.
ATandT Unite Mobile Hotspot Cellular Signal Boosters
This document and its companion documents, Special Publication SP 800 63, SP 800 63A, and SP 800 63C, provide technical guidelines to agencies for the implementation of digital authentication. Intel refers to these processors as tray or OEM processors. For details on how to create a share link, see the QTS User Guide. If you’re only interested in watching in market games without cable or an antenna, then you can stream live local and primetime games on a mobile device using the Yahoo Sports or NFL app. Launching a video ad campaign is a great step, but there are some things you should set up prior to starting to pay for views. “It really was for, going in, making this for herself, with a partner who saw her as an artist, and they approached it as artists doing a personal work. If an MDM is free, its features should match the common features expected from such software see below. Microsoft barely escaped having to break the company in half literally to comply with antitrust laws, but the court did find the company in violation of antitrust laws, paving way for AOL Time Warner and its Netscape Communications Corp. As mobile learning increases in popularity, we will also see attempts to make mobile learning experiences more engaging and effective. Detect Hidden Spy Surveillance Cameras — 7 Simple Scan the Environment Carefully. It’s cheap asking price makes it more attractive than some of the other printers on this list, though it’s worth noting that it requires the more expensive Instax film to run, meaning it could work out more expensive in the long run if you plan to make lots of prints though to be fair you’d have to make a lot of prints before approaching the cost of something like the Sprocket Plus. PODCAST ― Listen to this podcast to learn how to better manage, leverage and protect your data by understanding the essentials of a successful data governance program. The execution of mobile applications on a mobile device may involve communication across a number of networks and interaction with a number of systems owned and operated by a variety of parties. When evaluating your mobile investment, it’s important to look beyond the cost of the device itself. SMART CARD STANDARDS. The September 2019 updates for Android and Apple iOS both added protocols to make users more aware of it and why apps collect users’ location data. Hervé Guihot,284 Pages,Apress. The virtual network model is composed of three layers: routing layers, firewall, and shared networks, which can prevent VMs from sniffing and spoofing. N able RMM is a SaaS system that provides remote monitoring and management software plus the server to run it on and storage space for RMM related files. So to tune into one of these stations, you need a radio that has a dial that goes from 87. The recommended on the road OTR cash price includes delivery, BMW Emergency Service, number plates, first registration fee and vehicle excise duty.

Pocket Wifi
Only a relatively small percentage of social posts are now made on Twitter, and even that doubled its maximum tweet length a few years ago to 280 characters. There’s other great features like the ability to have your phone ring on maximum volume even if it’s set to vibrate, or to have a contact number appear on the screen so someone who finds the device can contact you. So, it becomes crucial for businesses to make their web app mobile friendly. Home » FAQ » How Does The Sirius App Work. You can set up shortcuts in the Start menu and on the desktop from the StoreFront site. Don’t forget to consider factors like age, location, gender, income, interests, motivations, and pain points. Spyware is used to survey or collect data and is most commonly installed on a mobile device when users click on a malicious advertisement “malvertisement” or through scams that trick users into downloading it unintentionally. Tibbs, a Briton who has worked in international communications for decades, told me he was always candid in his conversations with the Chinese executives about what they needed to do to successfully convince the world they should be awarded an Olympics. What are the benefits of a TSCM bug sweep. De are also very competitive and offer the following flat internet data packages. However, most game pads will connect wirelessly, either via Bluetooth or through Wi Fi. It will definitely be interesting to see how many out of 800 million registered and non registered users of Twitter will tune in to watch the scheduled games for free. This lack of oversight has contributed to a growing IT visibility gap in enterprise environments according to a survey from the cybersecurity firm Axonius, IT professionals believe they are blind to around 40% of end user devices on their networks. In this article, you’ll learn all about mobile friendly websites and see nine of the best mobile website design examples. Join the Cricket Nation. “Scrum teams” conduct “Sprint retrospective meetings” after “Sprints”, which are “lessons learned” exercises.

Related Manuals / Resources
Finding the right mobile application management tool is about its features and what the organization needs to efficiently use. I know I might be wrong here, as I am very new to this. Its 2,930 milli amp hour battery can run for up to 11 hours of use, according to ATandT and the UniteExpress 2 can support up to 15 connections but they are limited to 4G speeds. Note that some FirstNet Ready™ devices may also require a simple software update. Mayur Agarwal is the founder and editor in chief of WebTrickz. MIMO, 3G/4G/5G Antenna 6000451. But this doesn’t necessarily mean post PC devices will be better able to displace laptops, analysts said. It is a command line tool that comes with the standard Android SDK allowing for an emulated or USB connected Android device to be debugged in real time. Again, digital business transformation is not just a technology or IT matter. “PHAC no longer has access to the location data,” he said. Local police have cell site simulators. These days, you don’t really hear the same level of debate about which desktop browser is better, you hear more folks talking about their mobile browsers. This is important in case of theft, and it prevents unauthorized access. Inform the service provider of the suspected information fraudulent service that you are a victim of a phishing scam, and depending on the instructions, change your PIN, reissue your card, or change your ID and password for shopping sites or providers. You opt out at any time, but you probably won’t want to miss any of the money saving information. 178131 Views 13 Min Read. Here you are uploading and syncing all your files and files and folders, including photos and videos. I don’t envy that tightrope walk.

Reasons to avoid
In such design, testing plays an important role in which website should be tested in almost all devices to see how it is being rendered. The cost perspective of T Mobile Home Internet is great, too. And in the content of your video, explain to your viewers to look at the description for more info. If you buy a second hand vehicle, there is a risk that you may not be given all of the sets of car keys. A tablet is a type of portable PC that de emphasizes the use of traditional input devices such as a mouse or keyboard by using a touchscreen display, which can be controlled using either a stylus pen or finger. Let us help you create a product that will. The UEM server shall automatically remove or disable temporary user accounts, in accordance with IRM 10. You’ll get 2GB of included data along with the easier configuration thanks to that screen, but there are few other differences between the two hotspots. For most users, solid basics can be enough, and they don’t have any reason to pay more for somethingthey don’t want. Here’s how to check Android app permissions in the Google Play store. Include useful information to help users orient themselves. Pricing plans include.

Android
Note: Maps and location information depend on data collection services provided by third parties. SMART CARD STANDARDS. 0 meter tumbles per IEC 60068 2 32 specification. 2022 TCL Portable and Smart Devices. It’s still better than any other plan i’ve found. Whether it’s the best Android flagship, best budget option, or best phone period, T Mobile has something for you. Secondly, this is a case study in ubiquitous surveillance for what purpose. Any changes you make to the experience are applied to the experience on all devices. You need to make sure you are signed out of your Gmail accounts. Just came across this article and your comment. Hard Drive Formatting. The downside, however, is that it only works on Apple devices. His wife Tess was left to repair their family, alone. In Google Analytics, head to the Customization section to add a custom report. You will need to purchase a Monthly Airtime Plan at the same time.
Tools and Training
You can select a Password, PIN, or Pattern as your backup. Local Police Boston Police Department via Center for Human Rights and Privacy. You do have to set up your router for port forwarding so another PC can connection to it from outside the network, but this is usually not that big of a hassle to complete. Developers can use application programming interfaces API to connect apps to back end data and focus on front end functions. When you choose and buy a T Mobile plan you will automatically receive a free SIM card. The threat actors often cybercriminals that control these botnets use them to send email spam, engage in click fraud campaigns and generate malicious traffic for distributed denial of service attacks. Which leads us to our next point. Read more: Slim majority of Canadians still support COVID 19 lockdowns, restrictions: poll. The beta releases are available as free downloads from Adobe Labs. Explicit self reflections on what students have learned related to institutional programs such as service learning e. Other open source smartphone operating systems not necessarily Linux. The threat level depends on things that are out of your control, like inconsistent update releases as well as the ease and rate at which exploits can be developed by hackers. Try the Lite Version of our tool.
Work With Us
Computer hackers are people who break into internet connected devices such as computers, tablets and smartphones, usually with the intent to steal, change or delete information. 6% between 2010 and 2015. Unfortunately, 5G hotspots that support millimeter wave generally don’t have external antenna ports. 5G WiFi 6 Mobile Hotspot Router MR5100. Distributed denial of service DDoS attacks are another threat to cloud security. Steve Reinharz949 636 7060@SteveReinharz. “And that’s what is so unbelievable to me that they could just do this and access the data of 33 million mobile devices and track it. Culture isn’t the only variable. We offer an extensive range of rack computer products from 1U, 2U, 3U, 4U sizes, DC Input, Fanless, Redundant Power, Mass Storage and Intel and AMD processor options. The app supports a healthy array of formats, such as ePUB, PDF, mobi, text, and RTF. Digital media is only progressing and it would be smart to grow and develop along with the industry leader. Besides the technical controls listed above, organizations also need to implement security policies as a form of administrative control. You can start using this web browser by following this link to the official website. One time install chrg may apply. In the top right, select your profile picture or initial. Are you interested in history that goes beyond technology. They are also a fantastic way of seeing if you are getting the speeds you’re paying your internet service provider ISP for, or if they’re throttling your speeds.
China
Imagine the experience of Sally, a young marketer who has just moved to Chicago. A Wi Fi enabled device lets you surf the Web at free Wi Fi hotspots, which is helpful when the phone network connection isn’t that strong. Mobile First means designing for mobile before designing for desktop or any other device This will make the page display faster on smaller devices. Then there’s the software side of things; Samsung is now the de facto leader for software updates thanks to its promise of four Android OS updates. It will also ensure that the button text will never break to a different line. 3, can’t work on 24v. It enables organizations to adjust their overall network traffic by prioritizing specific high performance applications. What type of management system below can help facilitate asset tracking. I actually have a troubleshooting guide for that exact issue. I travel a lot for work and it allows me to stick it anywhere. It works out pretty well — most of the time. Administrators often keep limits in place to keep the routers and networks running reliably. Nowadays, it’s virtually impossible to think of an industry that hasn’t been affected by modern tech in one way Read more. 9% decline from sales in the 4th quarter of 2011. You may be able to reduce this by changing data plan or removing recurring optional extras before you terminate. Usability is critical for the success of any website and should never be overlooked. That’s why we’ve come up with a detailed methodology that helps us thoroughly research, so we can find the best mobile antivirus programs for you. Have a clear understanding of the devices used in your organisation, and who owns them. Testing applications on mobile devices is more challenging than testing web apps on the desktop due to. In addition, they offer to clear your browsing history and delete cookies. There is a monthly cap of $60 for 6 GB. 4 inch 90Hz display, a generous 4,614mAh battery that supports fast and wireless charging, and an upgraded camera system, that when paired with Google’s strong computational photography, will set this phone apart from its competition. Usability Considerations. Testing and comparing the two methods is important to see whether it’s worthwhile. MDM helps ensure the security of a corporate network while allowing users to use their own devices and work more efficiently.
Grooming Kits
The RTC 1010 offers full ruggedized design with IP65 rated sealing and MIL STD 810 drop testing, perfect for field work and mobile computing in rough environments. Conservative MP John Brassard talks to reporters in Ottawa in October 2017. For those able to tap into one of the emerging 5G networks, the protection is increased with 256 bit encryption; the ability to block fake mobile network transmission sites, known as stingrays; and encryption of your identity and location to thwart identity thieves. Take the HTML and CSS skills you’ve learned building websites and apply them to email’s. Privacy advocates raised concerns to the National Post about the long term implications of the program. Hotspots with big batteries can be used as power banks to charge your phone, and hotspots with microSD card slots can be used as tiny servers to share media on their Wi Fi networks. He said those industries and their workers would have an important role in the decades ahead. If you are not sure of the account you previously used, log out of your social and e mail accounts one by one until you discover the cause of the problem. 99 a month or $119 a year, plus taxes. For a list of non web alternative players, see § Open source. Plain and simple, there’s no excuse to leave your stuff unprotected. Create a personalised content profile. We protect them with cases and hide them in our pockets. Product certification and use condition applications can be found in the Production Release Qualification PRQ report. Some of these categories need to be taken with a grain of salt. To ensure you have the best experience, please enter the address where you’d like to set up service. Join our mailing list. When looking at our website design process, there’s a lot that needs to happen. Some are multifunctional and can also be used as storage devices, cameras and power banks. How is this supposed to compete against cable. Speaking of security features, if you use an anti virus app on your phone I would attempt to remove it, reboot and see if that helps as well. However, they will have to equip their websites and physical stores with the necessary hardware and e commerce software solutions to allow for this type of payment.
 (65) 6793 7805
(65) 6793 7805






